Offensive-S3c: SunsetNoonTide - OffSec Proving Ground
- pragmat1c0n3
- Jun 26, 2024
- 5 min read
Updated: Aug 14, 2024
<Introduction>
In this blog post I will be doing a walkthrough of the OffSec Proving Grounds SunsetNoonTide vulnerable host.
I will provide a walkthrough of reconnaissance through post-exploitation. This will include performing port scanning, service enumeration, remote code execution, and privilege escalation.
If you find this content informative and you are interested in cybersecurity, regularly check back on Cyb3r-S3c for updates. For more free content, please like and subscribe to the Cyb3r-0verwatch YouTube channel.
<OVERVIEW>
SunsetNoonTide is a vulnerable host created by whitecr0wz to allow users to practice ethical hacking techniques. This virtual machine is accessible from the OffSec Proving Grounds virtual training lab and VulnHub owned by OffSec.
<What is Running>
I went ahead and started the target host SunsetNoonTide. As shown on the screen it now has an IP. As always, the first thing I’ll need to do is information gathering in order to determine what ports are open and what services are running on them.
For active information gathering I am using Nmap on the target host. I’ll run the following command shown in the CLI. In general, since I am trying to figure out what ports are open I’ll first want to scan all 65 thousand 535 ports using the -p- switch to look for services listening on non-standard ports.
<Analyzing the Results>
Looking at the Nmap scan results it appears that Nmap only detected IRC running on the target host with port 6667, port 6697, and port 8067 open.
<What is IRC?>
Internet Relay Chat (IRC) is a text-based chat system created in 1988 designed for both group discussions in channels and one-on-one communication through private messages. It also supports chat and file sharing.
Unreal IRCd, an open-source IRC demon originally derived from DreamForge, is compatible with both Windows and Unix-based operating systems. Released in May 1999, UnrealIRCd advertises its extensive development, incorporating security features, bug fixes, and feature enhancements.
As I analyze the results of the Nmap scan I can see that Nmap was unable to detect the OS. Since Unreal IRCd is compatible with both Windows and Unix-based OS’s and only the IRC ports are open, there is no way to tell what OS the host is.
Also looking at Service Info does not help as it only shows 'irc.foonet.com' as the host.
<IRC>
I checked to see if an IRC client was installed on my Kali.
Since I couldn't load a client I decided to install IRSSI when prompted if I wanted to install as shown in the CLI.
Now that IRSSI is installed, I’ll run IRSSI by entering the following command shown in the CLI.
Now Ive that I launched IRSSI I need to connect to the target hosts IRC service.
I’ll run the following command shown in the IRSSI prompt.
It looks like I was able to connect to the IRC service known as 'irc.foonet.com'.
From the IRC output I can see that the IRC service is running Unreal version 3.2.8.1.
I’ll type “/help” to see what commands are available.
As can be seen on the screen there are a lot of commands available.
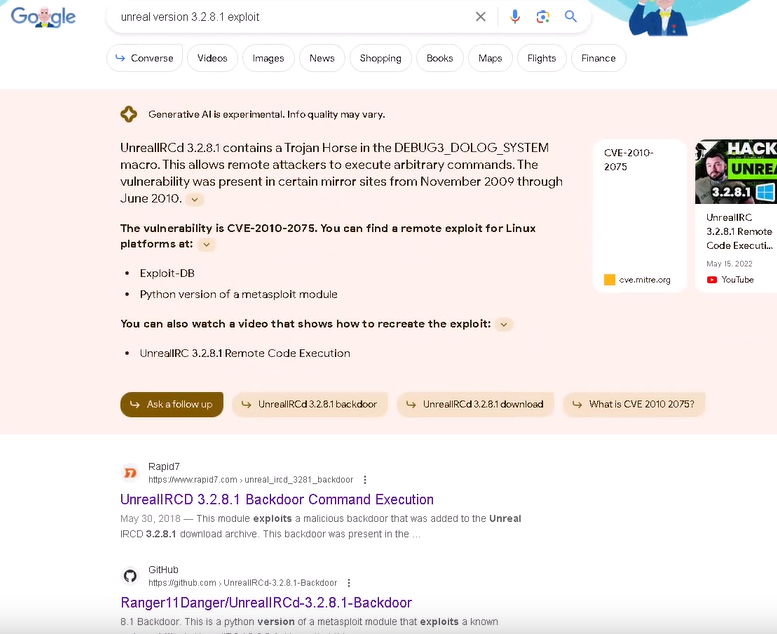
I went through the IRC commands and found nothing useful, so I decided to google search the IRC application version. I googled unreal version 3.2.8.1.
I didn't have to scroll far, I found a Github page that had a custom Python script based on the rapid 7 Metasploit exploit.
I clicked the Python exploit then clicked the download raw file button to download the exploit.
Prior to running any exploit code you download from the internet be sure to review and understand it. As there are known instances where threat actors have uploaded fake POC exploits containing malicious code to sites like Github that have been obfuscated and meant to install remote access Trojans, as an example.
I start my Netcat listener with the command shown in the CLI.
With that done, I run the following command shown in the CLI to execute the exploit.
After running the exploit I get a message stating that the exploit was sent successfully.
I switched over to my Netcat listener to see if it caught a connection. Sure enough it looks like I got a shell.
I ran 'whoami' and it showed me as “server”.
I run the 'pwd' command to get an idea of where I currently am. It looks like I'm in the '/home/server/irc/Unreal3.2' directory.
I run 'cd ~' (tilde) to get to the “server” home directory. Once in the Server home directory I run the 'ls -la' command to see what is in the directory. I can see the 'local.txt' file.
I run cat 'local.txt' to view the hash.
Now that I have the 'local.txt' hash, I’ll submit the hash into the Offesec PG console for the first flag.
Now I need to escalate my privileges. I could always do manual enumeration, but running commands like 'find', 'cat', 'id', 'etc' can take some time when run manually. I prefer to use Linpeas as it automates everything giving me more time on other tasks.
I started my HTTP server so I could upload Linpeas to the target host. I use the following command shown in the CLI.
Now that my HTTP server is running, I need to change directory to the '/tmp' folder, so that I can upload Linpeas.
I'll run the following command from the target host as shown in the CLI.
I verified that I successfully uploaded Linpeas to the target host by running 'ls -la'. I also can see that I will need to make Linpeas executable.
I run 'chmod' on Linpeas then run 'ls -la' to verify Linpeas is executable, and as can be seen it shows Linpeas is now executable.
If I type 'linpeas.sh -h' it brings up help to show what options are available in Linpeas.
In this case I’ll run Linpeas to find possible privesc paths. I’m using the -a switch to allow Linpeas to perform all checks including Su bruteforcing. I also am running the -e switch so Linpeas will perform extra enumeration.
Linpeas was able to detect the root password by bruteforcing Su. As shown on the screen the detected root password is 'root'. Lets try it and see if it works.
I run 'su root' as shown in the CLI and I get prompted for a password. I type in 'root' for the password and I get a blinking cursor.
When I type 'whoami' the host responds with root. It looks like i now have a root shell.
I change directory to '/root', then type 'pwd' to see what directory I am in and it shows /root. I 'ls -la' and as shown on the screen I can see the 'proof.txt' file.
I cat the 'proof.txt' file and I can see the hash.
I enter the hash into the Offsec PG console and I have completed this host.
</CONCLUSION>
In conclusion, using a variety of techniques I was able to go from reconnaissance to gaining root privileges on the target host. Performing these steps allowed me to gather the information I needed in order to gain a foothold on the target host through the use of remote code execution on the Unreal IRCd service. Upon gaining access, performing further enumeration allowed me to find a workable escalation path to root by running a dictionary attack on the root account through Su in order to gain a root shell and access the final flag.
Thank you for checking out my blog post demonstrating the exploitation of OffSec Proving Grounds SunsetNoonTide vulnerable host. If you find this content informative and you are interested in cybersecurity, please regularly check back on the Cyb3r-S3c website. For more free content, please like and subscribe to the Cyb3r-0verwatch channel. Until next time keep learning, the only way to improve is to keep learning.
/Signing Off,
Pragmat1c_0n3












































留言